What Is Native Behavioral Biometrics? How It Secures Digital Identity Without Friction
Native Behavioral Biometrics: Supporting Seamless and Secure Digital Identity
In the ever-evolving landscape of fraud prevention and digital identity verification, businesses are constantly seeking solutions that strike the perfect balance between security and user experience. One of the most promising innovations in this space is Native Behavioral Biometrics, a powerful, frictionless approach to understanding and verifying users based on how they naturally interact with digital platforms.
In this blog, we’ll explore what Native Behavioral Biometrics is, how it works, its advantages over traditional fraud detection methods, and why it is a must-have in today’s digital ecosystem.
What Is Native Behavioral Biometrics?
Native Behavioral Biometrics is the process of analyzing and profiling the unique, subconscious behaviors of users as they interact with websites, applications, or digital platforms, without the need for additional data collection or hardware. It measures patterns such as:
- Typing cadence and speed
- Mouse movements
- Touchscreen gestures
- Device orientation
- Scroll behavior
- Tap pressure and swipe dynamics
The key word here is native, meaning that the technology runs seamlessly in the background, embedded directly into a business’s fraud prevention strategy, without disrupting or altering the user journey.
Darwinium has in-built behavioral biometrics capabilities, available across the customer journey and on every field of a form input. This data can be used within features, rules and models to enhance risk decisions.
Businesses Can:
- Monitor the way a user interacts with their devices across web and mobile to detect bot-like behaviors and indications of remote access software.
- Characterize how a user types on a keyboard, including use of shortcut keys, to detect potential high-risk behaviors, such as copy / paste or unusual hesitancies on specific pages or fields.
- Harness mobile sensor data including orientation and accelerometer for indications of live calls and signs of potential social engineering.
How Can Native Behavioral Biometrics Work for Recognizing Good Users and Identifying Fraud?
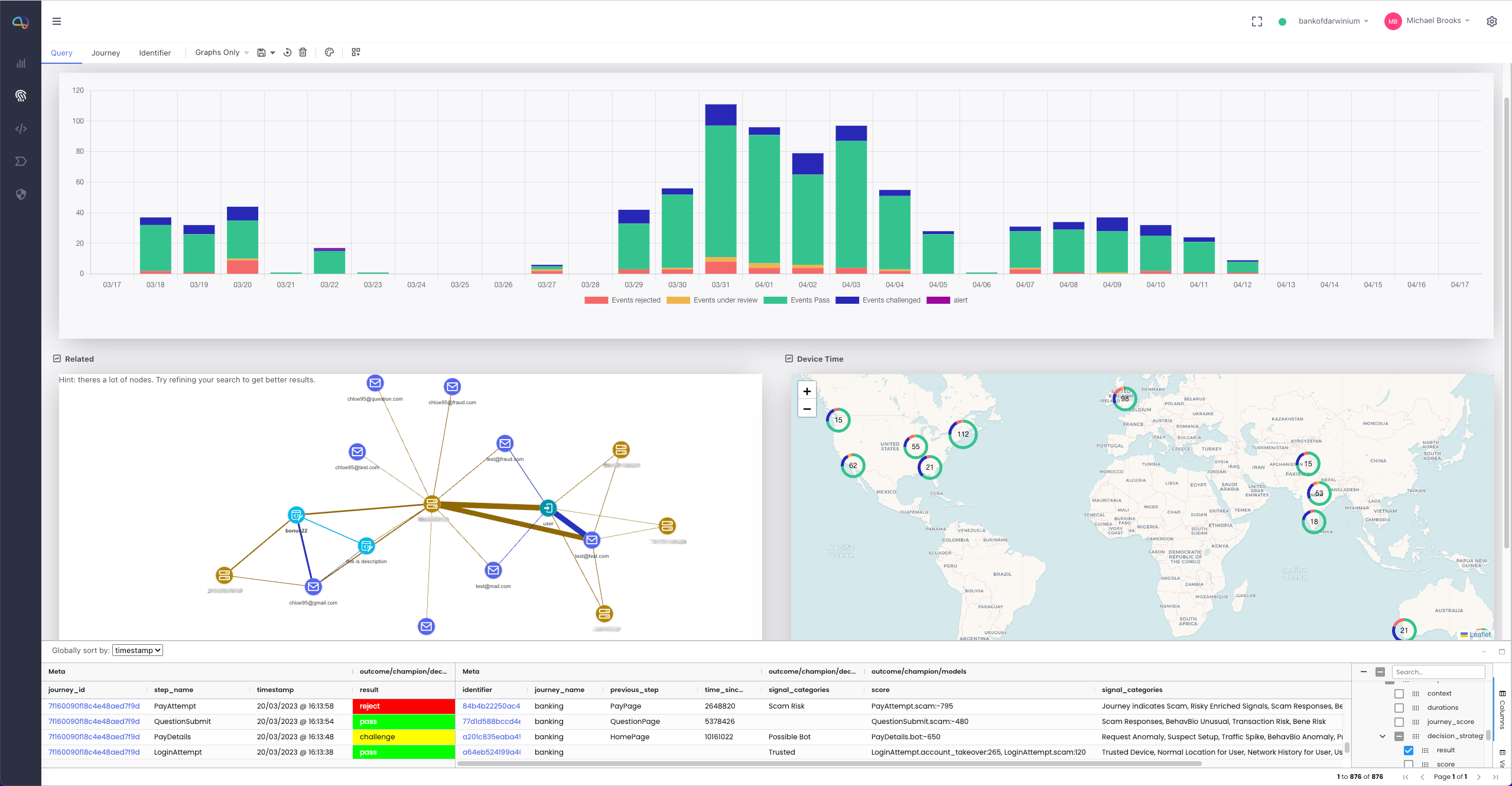
At its core, Native Behavioral Biometrics collects information about how a user interacts with their device. This can then feed into machine learning models to build a behavioral profile for each user over time. Here’s how it typically works:
- Continuous Data Collection: Behavioral signals are passively and continuously collected during a user's interaction, whether during login, checkout, or browsing.
- Behavioral Baseline Creation: Platforms like Darwinium can then learn what "normal" looks like for each user. For example, how quickly they type their email address or how they scroll through content.
- Risk Scoring in Real Time: Each session is evaluated against the user’s behavioral baseline and population-level trends to detect anomalies.
- Decisioning and Response: If abnormal behavior is detected, the system can flag the session, trigger step-up authentication, or block the interaction entirely, all without interrupting genuine users.
Why Is Native Behavioral Biometrics Important?
1. Frictionless Security
Unlike traditional multi-factor authentication (MFA), behavioral biometrics work silently and continuously in the background. Users don’t have to enter one-time passwords or answer security questions, resulting in minimal friction.
2. Mitigation of Emerging Threats
It can be highly effective in supporting strategies to more accurately detect:
- Account Takeover (ATO) attempts
- Credential stuffing attacks
- Social engineering scams
- Bot activity and scripted behavior
3. Privacy by Design
Behavioral biometrics is capturing how a user is behaving and interacting with their device, rather than any specific PII data relating to their identity.
4. Device & Channel Agnostic
Native behavioral biometrics can be embedded across web, mobile, and app environments, making it highly scalable and adaptable.
Integrating Behavioral Biometrics into Traditional Fraud Detection
There are several key benefits to layering behavioral biometrics with existing fraud detection protocols. These include:
- Continuous, Passive Authentication
Behavioral biometrics analyze how users interact with a device, for example mouse movements, typing rhythms, touch gestures, and more, continuously throughout a session. This allows for:
- Ongoing validation of a user’s identity after login
- Detection of account takeovers and session hijacking
2. Detection of Sophisticated Fraud Patterns
Legacy systems often rely on static rules or basic device fingerprints. Behavioral biometrics enhance detection by identifying:
- Human vs bot behavior
- Social engineering (e.g., remote access)
- Behavioral changes in legitimate users (e.g., signs of coercion)
3. Minimal User Friction
Unlike step-up challenges (OTP, CAPTCHA), behavioral biometrics operate invisibly:
- No impact on user experience
- Increased conversion rates for genuine users
Use Case Example
Touch Attributes
Darwinium Digital Signatures uncovered networks of linked bonus abuse behavior even when cookies were cleared, IP addresses were switched, or devices were obfuscated to look like a new user.
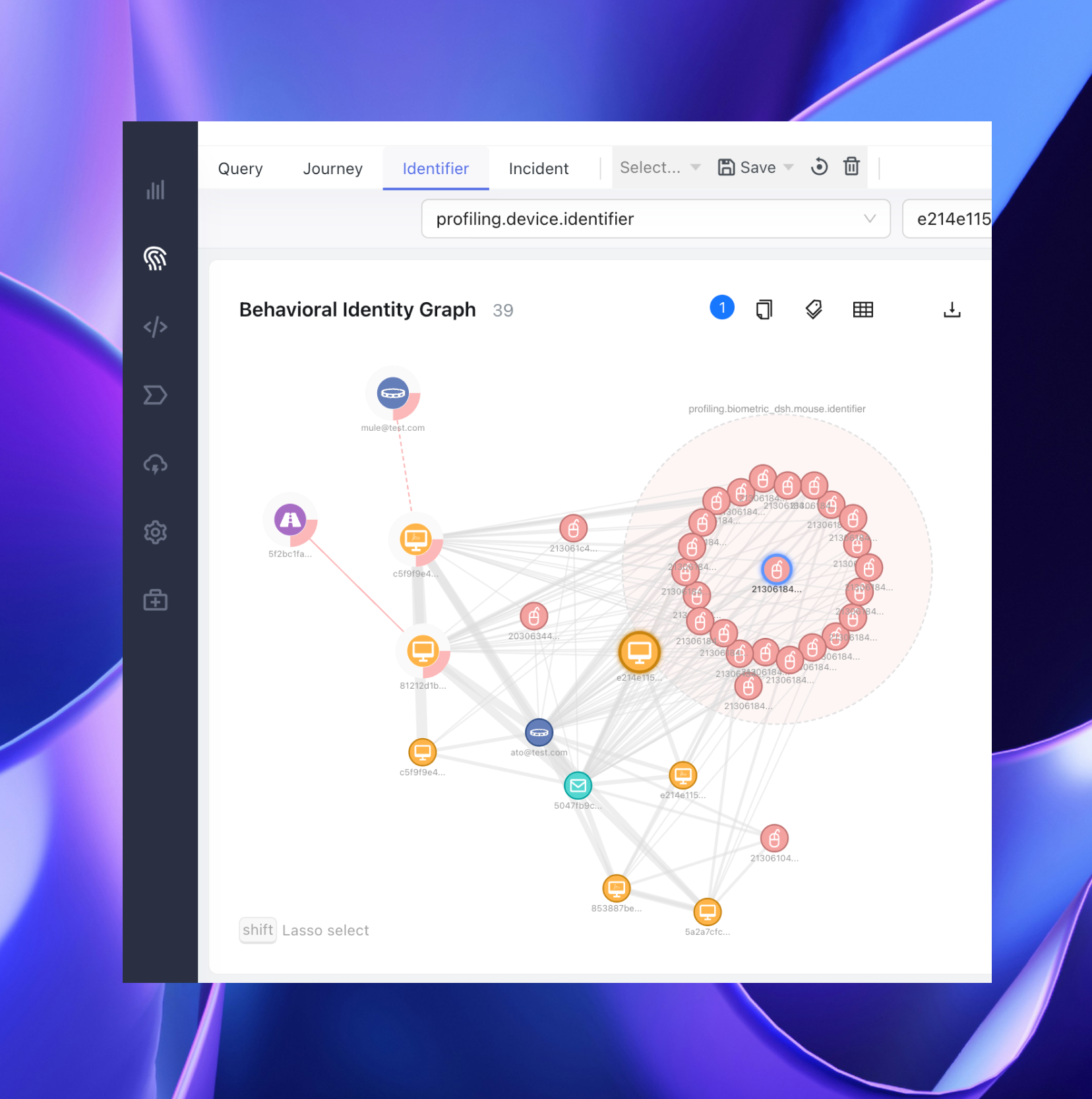
One such network was a fraud farm of over 22,000 users. Darwinium identified that key behavioral biometric indicators differed by a factor 5-10 x between known fraud farms and the general population, allowing for easy differentiation.
Final Thoughts
As fraud tactics evolve and digital transactions become more complex, businesses need to adopt innovative, user-friendly security measures. Native Behavioral Biometrics are a critical layer in modern fraud prevention strategies, offering context-rich, intelligent detection without sacrificing the user experience.
If you're looking to future-proof your digital security strategy while delivering seamless customer journeys, it’s time to consider integrating Native Behavioral Biometrics into your technology stack.
Using Behavioral identification to Separate Trusted and Risky Users Online
Download the Whitepaper
