AI Fraud Prevention Across the Entire Customer Journey
AI Fraud Prevention Across the Entire Customer Journey
Detect and defend against AI fraud, scams, and account abuse in real time - across complete customer journeys, not just transactions - without disrupting trusted user experiences.
Understand Intent. Stop AI Fraud
Understand Intent. Stop AI Fraud
Darwinium is an AI fraud prevention platform that deciphers intent across every digital touchpoint. It combines adversarial AI agents that simulate real-world attacker behavior, behavioral identification to distinguish trust from risk, and an AI Copilot that proactively recommends tailored remediations. We protect banks, eCommerce merchants and fintechs from threats that evolve faster than traditional release cycles.
Unite Operational Siloes
Your cyberfraud AI system of record - uniting rich data across the entire customer journey with adaptive risk decisions; to align security, fraud, and customer experience teams.
Create Customer Delight
Give customers - & their authorized AI agents - tailored digital experiences that build trust & lifetime value without unnecessary interventions.
Protect Against Evolving AI Threats
Use agentic AI simulation & AI-assisted remediation to close the gap between making decisions & taking action, without relying on IT/engineering resource.
Just Launched: Adversarial AI and Copilot Innovations to Harden Fraud Defenses
We’ve launched a new suite of AI capabilities to transform how AI-driven fraud is detected, understood, and remediated.
Darwinium Beagle uses autonomous AI agents to simulate complex adversarial behaviors, exposing hidden vulnerabilities across the customer journey.
Darwinium Copilot is an intelligent assistant that powers faster fraud remediation, smarter decisions, and seamless platform interaction.
Sign up for a live demo and learn more about Beagle and Copilot.
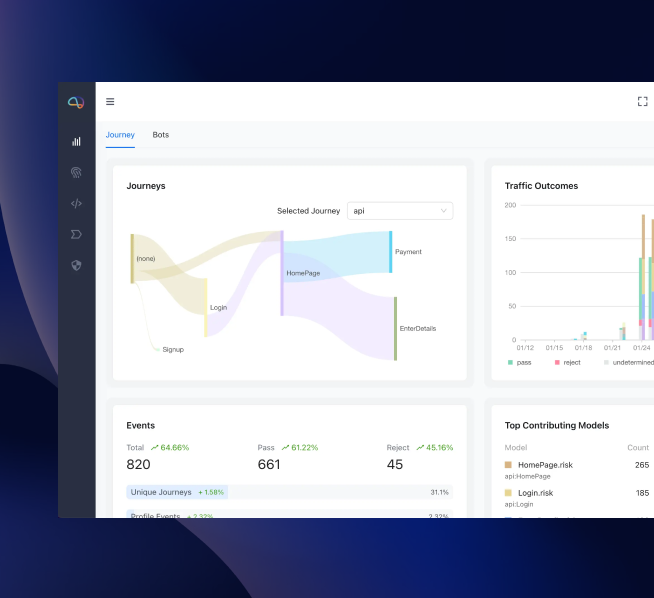
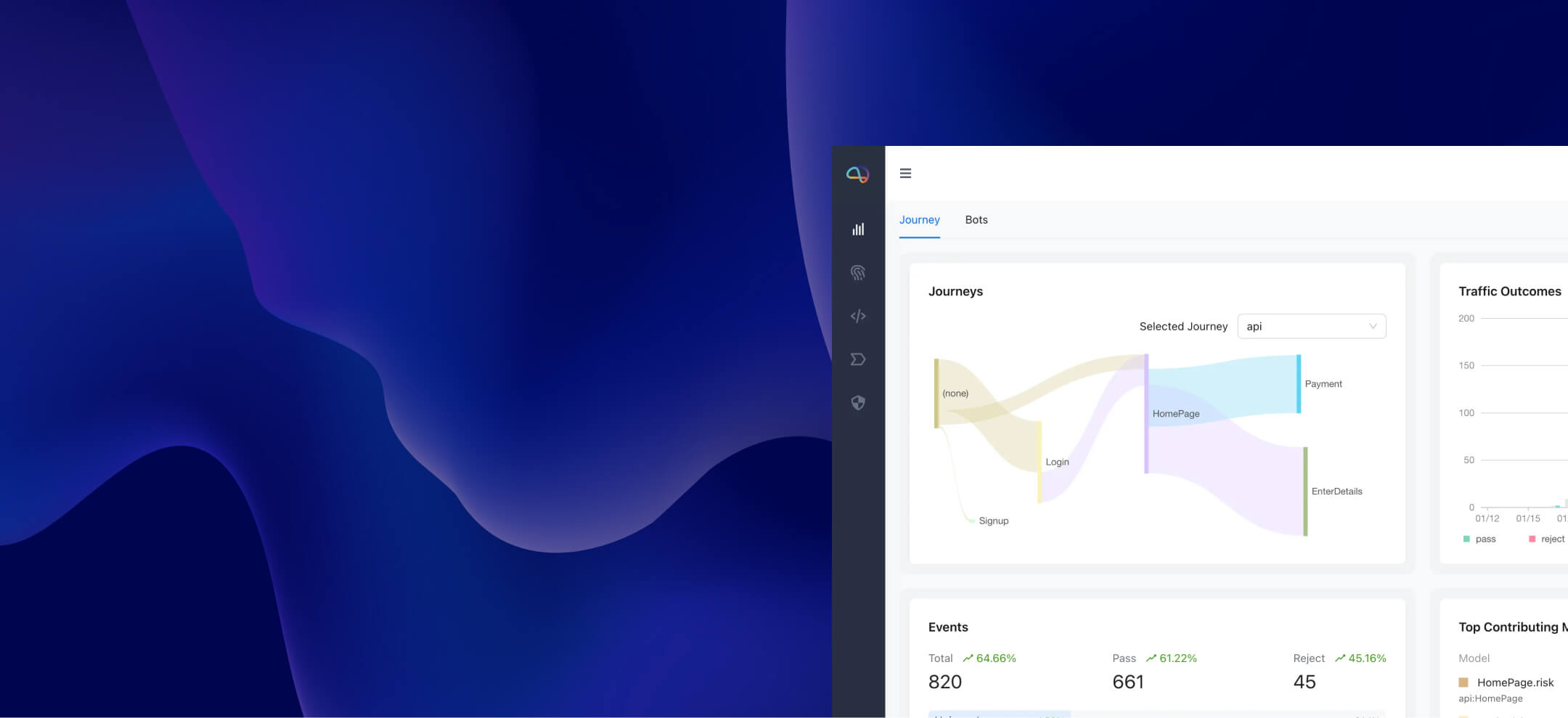
An Introduction to Darwinium
Understand true user intent, with full visibility of fraud and risk intelligence across security, fraud and customer experience teams.
Use Cases
Combine individual use cases across web, mobile and API endpoints, with full customer journey-level visibility
Account Security
Integrate one and protect every interaction. Analyze risks across pre-browsing behaviors, through to account creations, logins, details changes, checkout and payments.
Learn more
Fraud Prevention
Protect against account takeovers, payment fraud, shipping and returns fraud. Identify behavior indicative of scams and social engineering across payment journeys.
Learn more
Abuse Prevention
Prevent bonus abuse, business logic abuse and API abuse. Detect fraudulent or abusive content before it is uploaded. Protect end user trust and safety.
Learn more
Onboarding
Identify malicious automated bots and human click farms developing fake accounts. Streamline integration of third-party authentication / KYC checks for a slick onboarding experience.
Learn more
Account Takeover
Accurately identify returning users, even if device, browser or behavioral elements change. Separate trusted and high-risk behavior as it happens to prevent intrusion of trusted accounts.
Learn more
Payment Fraud
Add upstream context to downstream checkout and payment workflows. Consolidate digital interactions with instore activity, such as rewards redemptions, via the Darwinium API.
Learn more
Scam Detection
Detect subtle signs of social engineering or coercion indicative of a potential scam, via journey-level behavioral analytics and behavioral biometrics. Identify remote access behaviors, live call detection and unusual payment patterns.
Learn more
Bonus Abuse
Uncover unwanted bonus-abuse behaviors, such as use of automated bots that can bypass captchas, cookie wiping and use of private browsing to bypass device recognition, and use of proxies and emulators to generate multiple new player bonuses.
Learn more
Uncovering Hidden Fraud in Minutes with Darwinium
Darwinium helped us identify fraud on multiple seller accounts that we hadn’t identified before. This is a really great example of value Darwinium has enabling the traceability and exploration of a threat or issue through to solution in a matter of minutes.

Nikolaus Brauer
Software Architect

Industries
Enrich checkout risk assessment with upstream context. Build digital interactions that create loyal customers, while protecting against account takeover, payment, shipping and returns fraud.

Your Cyberfraud System of Record
Consolidate multiple data siloes into a single source of truth across the customer journey. Collecting data from CDNs, APIs, web and mobile apps.
Customer Journey Visibility and Protection
Deploy cyberfraud prevention at the perimeter edge. Add network, device, behavior and endpoint context to security tools, and complete journey-level visibility to fraud teams.
Encode Behavior into Identity Across your Digital Estate
Darwinium has distilled sophisticated device and behavioral interactions into industry-first digital signatures to better separate trust from risk. Simplify vast amounts of data into actionable intelligence that can be compared for similarity. Find patterns of behavior, identity, content and context.
Since implementing Darwinium, we’ve seen a significant improvement in our ability to detect and respond to suspicious activities - particularly around account takeover, mule detection and payment fraud scenarios. The real-time alerts, device intelligence, and behavioral analysis have proven to be extremely effective in helping us safeguard our customer accounts.

D'fiama Pandiyan
Fraud Operations Lead at Boost

See a live integration in real time to experience the simplicity of Darwinium's time to value
Book a demo today