Modeling User Journeys to Detect Fraud in Real Time
Beyond the Digital Transaction: Unmasking Intent Through Journey Analysis
Fraudsters use many methods to evade detection. And good customers can behave in unusual ways. Separating trust and risk is harder than it has been in the past. The holy grail is to look past standard transaction data, to uncover user intent. Read on for some insights into how Darwinium models a user’s behavior across multiple touchpoints in the digital customer journey, to determine their intent.
The way users interact with products and services online has changed irrevocably over the last decade. Simple payment or checkout interactions have been enriched with the ability to access rewards, bonuses, set up new payment details or shipping addresses, add new beneficiaries or accounts, browse new content, upload, list and interact with reviews or listings. This has made the concept of a digital journey more complex and nuanced than it used to be. Journey analysis now forms a key behavioral identifier that builds a picture of user intent and identifies fraud risk.
At Darwinium, we define journeys as: “an ordered collection of steps that a user takes in a web session, from the moment they land on a site until they navigate away”. Therefore journeys are composed of multiple steps, where we define a step as “a specific touch-point on a website, such as a specific API call, that a user lands on”. We utilize the concept of a journey as a first-class construct within our platform, to interpret and classify user’s behavior. This brings a number of benefits to both trusted users, and a business’s ability to better detect nefarious intent:
- Normal users can interact without unnecessary friction because their typical pattern of behavior can be modelled, and future transactions can be compared for similarity.
- When it comes to potentially malicious activity, this can be flagged or blocked in real-time, in particular with regard to emergent threats posed by AI agents and smart bots, that are able to learn from their environment and emulate human characteristics.
Using these two concepts we monitor user behavior on websites and are able to extract common user behavioral patterns from historical observations. Then we have developed inference techniques to highlight risky users from the rich observations of user journeys, comparing a single journey to both the general behavior observed across all users and from the user’s own previous behavior.
Why are journeys important for fraud use cases/behavior/edge deployments?
Most users follow predictable patterns when performing tasks on websites, with some natural variation. For example, my regular behavior when logging into a bank is to first check my account balance, and any recent transactions. However, if one day I log in and go directly to make an external money transfer, this is anomalous behavior for me, and with respect to the larger population. This presents an opportunity to identify and calculate probabilities of how far different types of user behavior on a website deviate within the realms of what we accept as “normal”.
Advanced Bots
These types of threats are particularly difficult to detect, with studies showing 95% of these threats not detected on websites. Moreover, malicious advanced bots are committing fraud attacks such as: account takeover, credential stuffing attacks, API abuse and payment fraud.
These bots are making automated pre-determined actions and are simulating human behavior, aiming to confuse analytics, such as the dwell time on pages and mouse movements. However, to achieve malicious actions efficiently they produce unusual patterns of traversing websites.
AI agents
AI agents are rapidly emerging in many fraud applications and are able to learn from their environment and change their behavior to reach their objective as defined by fraudsters. These agents emulate legitimate users, generating biometric data and images to pass identity verification, steal and test credentials from online sources, commit promotion abuse by generating new accounts, card not present fraud and SMS pumping on multi factor authentication.
However, not all AI agents are malicious. There is also an increase in the development of AI agents to automate tasks and optimize previously human-driven processes to drive efficiency gains.
Malicious human users
Human users conducting fraud — either acting within a fraud farm or operating individually — use methods like impersonating users, taking over accounts and siphoning money, committing promotion fraud, managing money mules through online banking, and manually creating many new accounts. These behaviors manifest as unusual journeys, such as proceeding directly to endpoints to make transactions, or exfiltrating money and personal details in a way that would be unusual for a “normal” user.
Benign users behaving unusually
Anomalous journeys can also regularly be from users that are benign, but may have taken an unusual journey due to a mistake, or perhaps resuming an action after a pause. We analyze the behavior of these types of cases and classify intent, to differentiate them from malicious anomalies to ensure that real traffic can proceed normally through a customer’s website.
Good users gone rogue
Accounts that have previously displayed normal behavior can suddenly change their behavior to undertake malicious actions. For example, when an account is sold or taken over by malicious actors, or if the current account holder is being coerced to take actions that are unusual, such as going straight to money transfers to send a large amount of money to a fraudster’s account. This sudden change would represent an abrupt departure from previous patterns and be flagged as an anomaly from the individual user’s historical behavior.
Attacks on specific API endpoints
Rather than going through normal journeys malicious attackers can mount attacks on specific API endpoints, but not via the usual initiation of a journey, for example bypassing the normal login steps to query endpoints that are contained behind the initial login step, possibly with valid credentials. These journeys can attempt to bypass normal protections that exist and perform malicious actions before defences can stop this behavior, with these types of journeys deviating from the historical patterns of steps, across all other users.
These differences in movement behavior allows insight into the intent of the event traffic, enabling additional context to be added to analyst investigations. Taking additional context from other observations and signals that are generated from the event data, we can classify the traffic into different categories to alert Darwinium customers. Defending against AI agents, advanced bots and malicious human users, while still allowing the real traffic to proceed even generated by non-malicious AI agents.
What capability have we added and what insights do we gain?
By analyzing the paths and timings of user journeys we calculate many probabilities to derive rich insights without relying on bespoke customer models and extensive training.
- How likely was the particular path taken by a user, measuring the probability of traversing the particular path compared to the regular paths. Unusual paths are taken by bots and AI agents exploring websites and SMS pumping.
- Measure differences of the recent transitions across all users against historical averages, identifying when many bots are exploring a customer’s site.
- Comparison between the distribution of average user and a particular user. By estimating the user’s distribution from limited data, we can detect the divergence of a user from typical behavior to better identify and classify risky users, and their intent.
- Estimating the probability of being in a particular state at a particular time, to identify users that are progressing through states quicker or faster than normal users, indicating automated behavior and possible spamming.
- Probability of the duration of journeys, identifying long delays for malicious human users potentially hijacking legitimate sessions.
- Probability of the particular number of transitions, that can indicate automated threats exploring a particular website or replaying particular steps.
- Probability of reaching a step in the specified number of transitions, identifying risks of malicious activity by identifying unusual fraudulent patterns, such as logging in and immediately going to add payee to make a transfer, and repeating steps such as credential stuffing, and SMS pumping.
Probability of reaching a step in a particular time window. This can detect the unusually quick paths through journeys that indicate risks from automated logins, as well as unusually long duration journeys that indicate repeated traffic through steps for session hijacking, and SMS pumping.
To communicate unusual journeys Darwinium has developed intuitive visualizations to drill down into why a journey was flagged as anomalous. The illustration below shows the total duration of the journey, the probabilities at each step in the journey, and the risk from each individual transition along the way.
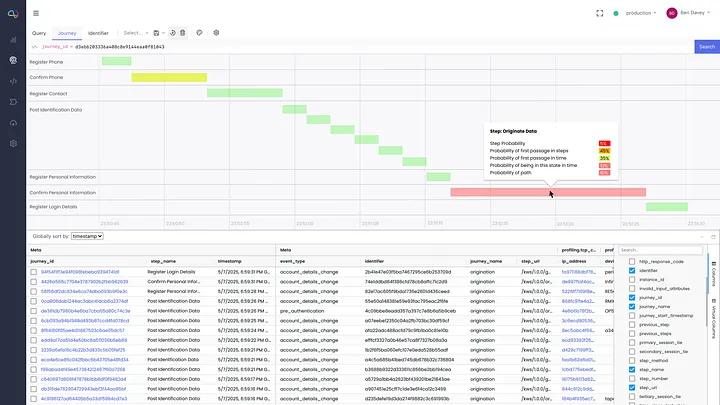
How do we model journeys?
With a limited set of data consisting of steps, their order and their timing of transitions we can construct models to calculate probabilities of how users traverse through the customer websites.
We can model the transitions by a customer as a process, X₁, X₂, …, Xₙ, traversing m steps, with the value of the nth step being iₙ ∈ {1, …, m}. Then we can model the journey probability by making a key assumption, the Markovian property, that the next transition only depends on current step that is
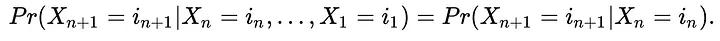
In statistics and probability theory this is the memoryless property and enables us to be able to calculate probabilities of reaching steps efficiently to detect anomalous journeys in real time. Given the probabilities of the next step we can create a matrix, P, the transition probability matrix containing the probability of transitions
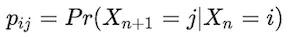
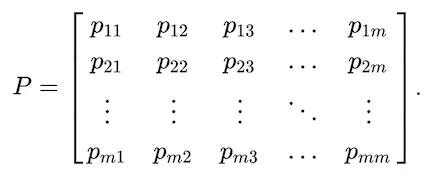
from specified steps i to j for any transition n as the i,jth element. Therefore we can create the probability transition matrix,
Then we can evaluate the probability of being in any step after k transitions by taking the matrix power of the transition matrix, Pᵏ, and extracting the relevant element
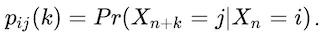
Viewing the transitions as a function of the number of steps, k,we perform analysis to calculate the probability of being in various states in different numbers of transitions.
Then we solve the hitting time probabilities in real time by solving the following set of linear equations for each step i to calculate the expected hitting times to all steps j.
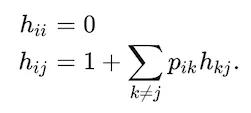
Where the first equation means that no time is elapsed moving from step i to step i, and the second equation means that we take at least one step if we’re not currently on the right step and the expected hitting time is the weighted average of the hitting times to all other steps.
We are able to estimate the distribution by inferring parameters of a hitting time distribution, using the mean hitting time. This enables us to calculate probabilities of the number of transitions in a journey, then block risky traffic and generate signals to assist analysts with fraud investigations.
In addition, we estimate the user’s distribution by using bayesian inference on the elements of the probability transition matrices, by taking the estimates and updating with user-specific data to model patterns at both the user and global level to highlight anomalous short and long term behavior of traversing websites.
In summary, modelling both individual user and website traffic journey behaviors can help businesses to better understand the full range of behaviors hitting their website, whether from human or machine, and with malicious or trusted intent.
